Businesses faced a rise in malware and ransomware attacks as COVID-19 made its appearance earlier this year. Now, after carrying out COVID-themed campaigns several months ago, Emotet – the world’s most costly and destructive botnet – is back, and it’s letting ransomware in. This week, we take a look at how businesses face and mitigate these threats so that you can Live Easy, securely.
What is ransomware?
Ransomware, under the malware umbrella, is a malicious software that prevents a user from accessing certain data or systems, and demands payment to grant that access again. Most common is encrypting ransomware, which replaces important documents with encrypted documents. Users pay for a key to decrypt the documents, which they can only hope to get, and in the worst (rare) cases, entire hard drives can be encrypted. Screen locker ransomware, on the other hand, denies users access to entire systems (computers, mobile devices).
The introduction of ransomware into a system often comes from infected PDF, Office documents, or URLS sent by email. These emails appear legitimate, and may even seem to come from a user’s company domain. As a result, ransomware poses an enormous threat to businesses.
Ransomware continues to threaten business owners
Businesses manage a large number of users, making ransomware threat mitigation more complicated. Even with clear company policies on managing suspicious communications, attacks happen. Just this month, Orange – the fourth-largest mobile operator in Europe with 266 million customers – fell victim to a Nefilim ransomware attack that targeted its service division, accessing customer data. Similarly, the University of California, San Francisco (UCSF), paid a ransom of $1.14 million to get stolen data back from the Nefilim group.
Ransomware attacks don’t show the usual signs of a malware infection. Encryption ransomware in particular works in the background with the objective of carrying out its malicious intentions before being noticed. This makes the attacks especially difficult to halt once company data has been accessed, and payment of ransom is often unavoidable. Software and cloud hosting solutions provider Blackbaud, for instance, managed to stop hackers from blocking corporate systems and fully encrypting files after a network breach. Still, with a subset of customer data accessed quickly by the attackers, Blackbaud was required to pay ransom to keep the leaked information confidential.
These ransomware groups are vicious, appearing and disappearing on a whim, and making their activities difficult to track. One such ransomware botnet is Emotet.
The Return of Emotet
That’s right: The world’s most costly and destructive botnet is back after a 5-month hiatus. Emotet was spotted Friday as it introduced a “blast of malicious spam” aimed at spreading the malware – incognito – with bank-fraud trojans and ransomware. The botnet sent out 250,000 messages in the US, UK, Middle East, South America, and Africa that contained the typical malicious attached document or link which, once accessed by a user, install the Emotet backdoor. Email samples provided on Twitter earlier last week looked like the following:
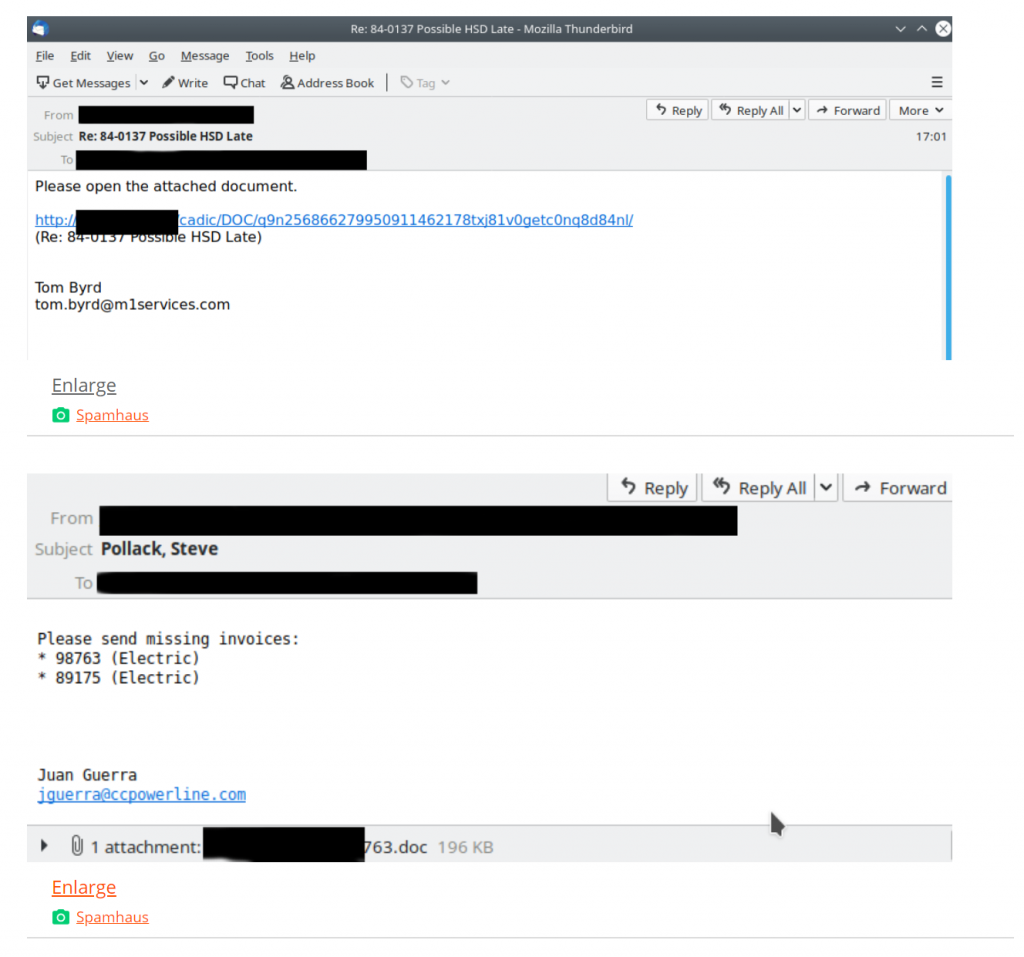
Emotet is known for taking long breaks with bursts of malicious messages over a short period of time. Its last appearance was back in February, when 1.8 million messages were sent out. So businesses beware: keep users vigilant of suspicious communication and attachments, and seek out the best defense.
The very best defense against ransomware
Antivirus/antimalware programs and security suites are efficient defenses against most malware attacks; they detect known threats, then use heuristic signatures and behavior-based detection to find new, similar threats. For the ransomware attacks that do make it in, bypassing those old-school signature-based malware detection programs, getting rid of them just won’t cut it once files get encrypted. In other words, removing the threat won’t get your files back.
While some security products do offer several layers of protection specific to ransomware, as PC Magazine Lead Security Analyst Neil J. Rubenking puts it, “the very best defense against ransomware” is “using an online backup utility to keep and up-to-date backup of your essential files”, and “the only reliable guarantee of recovery is maintaining a hardened cloud backup of your important files.”
At LeCiiR, we know that ransomware attacks have detrimental effects on businesses and productivity loss. That’s why we tailor our highly scalable and secure cloud infrastructure according to your enterprise network security needs, so that you can keep your important files backed up and Live Easy, securely. For questions on our services and how to keep your business safe from ransomware, don’t hesitate to contact us and leave your comments.

References
Catalin Climpanu, Cloud provider stopped ransomware attack but had to pay ransom demand anyway. July 2020.
Dan Goodin. There’s a reason your inbox has more malicious spam – Emotet is back. July 2020
Davey Winder. Orange, Europe’s Fourth-Largest Mobile Operator, Confirms Ransomware Attack. July 2020.
Louis Mosca. The Ransomware Threat Facing Business Owners. July 2020.
Neil J. Rubenking. The Best Ransomware Protection for 2020. July 2020.


Recent Comments